The U.S. authorities has launched a manhunt for a Russian fugitive with a $10 million reward on his head for operating the world’s largest ransomware scheme that attempted to extort thousands and thousands from notable targets such as Boeing and the UK’s Royal Mail service.
Dmitry Yuryevich Khoroshev, 31, of Voronezh, Russia, was the chief and developer of LockBit, a mercenary ransomware group employed out for cyber hits on organizations starting from nonprofits to hospitals to colleges, based on a federal indictment unsealed this week.
“Most individuals wouldn’t take into account being accused of making and administering probably the most damaging ransomware group on the earth as a badge of honor,” FBI – Newark Particular Agent in Cost James E. Dennehy stated. “Khoroshev, wears it like an Olympic Gold Medal.”
Khoroshev’s whereabouts are unknown. The Division of State introduced a reward of as much as $10 million for info that results in his arrest.
Lockbit ransomware, first seen on Russian-language-based cybercrime boards in January 2020, has been detected all around the world, with organizations in the US, India and Brazil amongst widespread targets, cybersecurity agency Development Micro stated final yr.
Reuters reported final yr that Lockbit hackers stated they’d obtained “a tremendous amount” of delicate information from aerospace large Boeing and would dump it on-line if Boeing did not pay a large ransom. Boeing confirmed in November that components of the corporate’s components and distribution enterprise had skilled “a cybersecurity incident,” however stated there was no menace to plane or flight security.
LockBit additionally threatened at one level to publish stolen information if the Royal Mail service in the U.K. failed to pay a ransom. In an e mail response to Reuters, Royal Mail stated proof from its investigation steered that the information allegedly obtained from its community didn’t include any monetary info or different delicate buyer info.
Khoroshev is charged with conspiracy to commit fraud, extortion and associated exercise in reference to computer systems; conspiracy to commit wire fraud; and eight counts of every intentional injury to a protected laptop, extortion in relation to info unlawfully obtained from a protected laptop and extortion in relation to intentional injury to a protected laptop.
The Justice Division’s unmasking and indictment of the Russian nationwide behind LockBit is the most recent in federal efforts to cease the ransomware group behind assaults in virtually 120 nations that extorted half a billion {dollars}, of which Khoroshev took 20%, based on federal prosecutors in New Jersey. 5 coconspirators have been charged and two are awaiting custody.
The announcement follows an operation in February by federal officers and regulation enforcement companies from the UK to disrupt to LockBit’s schemes, stated Nicole M. Argentieri, principal deputy assistant lawyer basic, in a video announcing the indictment.
The Division of Justice official referred to as the ransomware “a menace that assaults colleges, hospitals and different important infrastructure.”
A cyber gun for rent
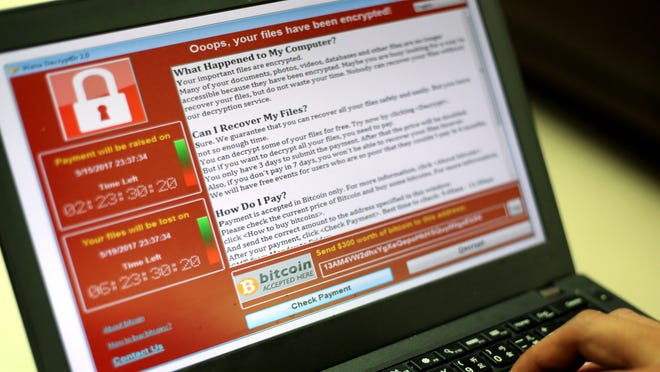
The ransomware, or software program, Khoroshev developed allowed criminals to steal a sufferer’s information and maintain it below the specter of publishing if the sufferer didn’t pay, based on the indictment.
The ransomware operates by utilizing quite a few strategies, akin to hacking or stolen credentials, to entry a sufferer’s laptop, the indictment says. Then, a customized model of LockBit is used to steal paperwork and information.
Afterwards, the criminals go away behind a “ransom observe” with directions on methods to get in contact for negotiations and a menace to publish if the sufferer doesn’t, the indictment says. Criminals demanded the ransom in Bitcoin, sometimes.
Khoroshev started growing and advertising and marketing the ransomware below aliases together with “LockBitSupp” and “putinkrab” in September 2019, based on the submitting. Third events successfully rented it to deploy on victims, however the Russian nationwide stored watch and even participated in ransom negotiations, the indictment says.
He marketed it on darkish internet cybercriminal boards, paying folks $1,000 to get tattoos of the LockBit brand as a type of company branding of types, and turned the cyber gun for rent “into a large legal group that has, at instances, ranked as probably the most prolific and damaging ransomware group on the earth,” the indictment says.
Extra:Global hacking campaign: Energy Department and other agencies hit by wave of cyberattacks.
Taking down “putinkrab”
After about 4 years of ransomware schemes, regulation enforcement companies from the U.S., United Kingdom and “world wide” left LockBit “virtually inoperable” in a coordinated strike in February, based on the indictment.
U.Okay. authorities reviewed seized LockBit information and found lists of patrons, victims and paperwork that supposedly had been deleted after the ransom was paid, the indictment says.
Of the two,500 victims, round 1,800 have been within the U.S. with at the least 55 in New Jersey, based on the submitting. Nonetheless, the vary of victims spanned from Argentina and Kenya to Finland and China.
Among the many victims famous within the lawsuit was a “multinational aeronautical and protection company headquartered in Virginia” that obtained a ransom demand of $200 million. Assaults have been pricey for victims to deal with and brought about misplaced income.
Additionally famous have been a Florida-based medical companies enterprise; a “main” Taiwanese semiconductor producer; a German automotive components conglomerate; and, in New Jersey, regulation enforcement companies in Passaic and Monmouth counties and a Somerset County college district.
After the February disruption, Khoroshev tried to launch LockBit once more. In an effort to beat out the ransomware competitors, he “communicated with regulation enforcement and provided his companies in alternate for info relating to the identification” of opponents, based on the indictment.
The Russian nationwide is quoted saying, “give me the names of my enemies.
Extra: Russian hacker charged by U.S. in ransomware attacks that raked in over $200 million.